Overview
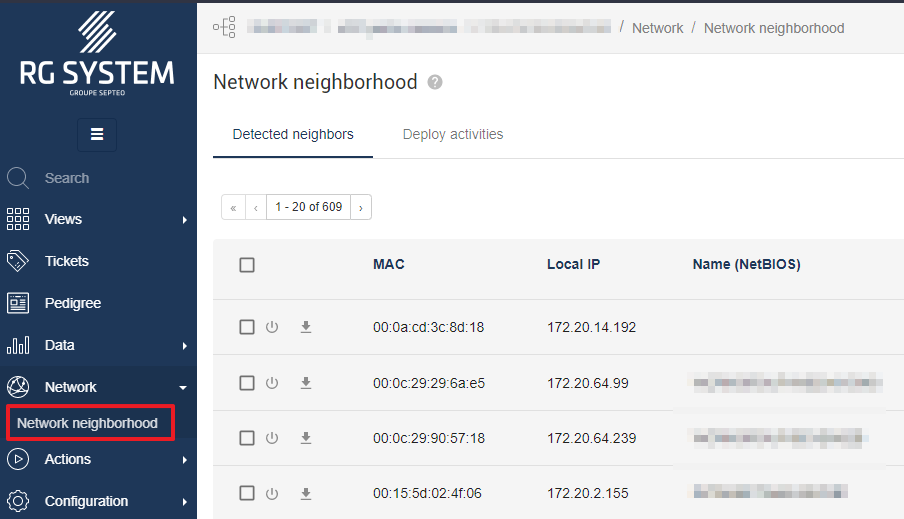
Network Neighborhood gives you a view of a server agent's local network. More precisely, it allows you to view all the machines that have communicated over the last 30 days with this server agent. This neighborhood is passively collected by reading the agent's ARP cache, then by regularly interrogating the detected neighbors to have some complementary data (Netbios name and OS type). Detected modifications are sent in quasi real-time. The last seen date of neighbors without changes are updated every 24 hours.
This feature is only available on server agents. If you only have workstation agents, you'll have to promote an agent to server to enjoy this feature.
MAC address
Each machine is identified by its MAC address. A MAC address correspond to a network interface of a machine. When a new MAC entry is detected for the first time, it is sent back to the dashboard in quasi real-time. A new alert is also available in the Heartbeat portion of the Alert page so that you can be alerted when a new item is detected (disabled alert by default).
MAC vendor
The data in the manufacturer column is derived from the MAC address.
Local IP
The displayed IP is the local IP on the network. This data is updated every second.
Tips: if the server is on several local networks, you can filter the machines of a precise network by retrieving on this agent pedigree the IPv4 address of the relevant interface, and by using that address in the filter of this column. For example : 172.20.64.234/16
Name (Netbios)
The Netbios name of the machine (if configured) is detected at the discovery of the neighbor, then every 20 minutes.
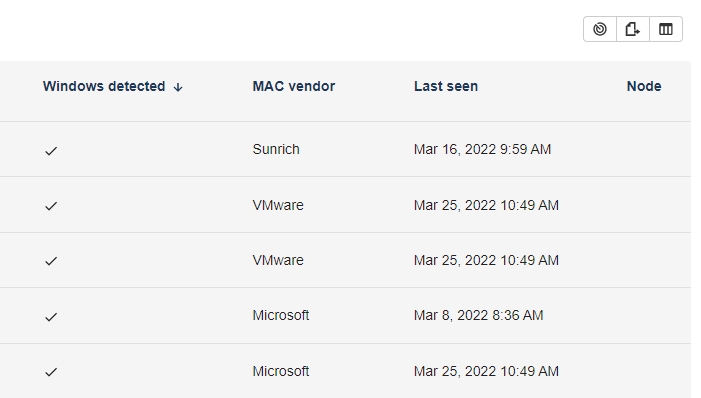
Windows detected
Detection of the operating system allow to distinguish Windows machines from other machines. It is based on the ping TTL setting, which is (by default) different on Windows OS. This detection is made at the discovery of the neighbor, then every 24 hours.
Beware, in order for this OS detection to work, ICMPv4 traffic needs to be authorized by the Firewall:
- On inquirer agent : File and Printer Sharing (Echo Request - ICMPv4-In)
- On neighbors to detect : File and Printer Sharing (Echo Request - ICMPv4-Out)
Last seen
This field shows the last time the agent has detected this neighbor. Unless there is a change in its other collected data, this information is updated only every 24h.
Node and Agent
The MAC address being the network interface unique ID, it allows RG infrastructure to easily detect whether a RG agent match this address. If it's the case, this agent will be referenced in those columns. Else you can launch a remote deployment, and its state will be displayed here.
Customization & Export
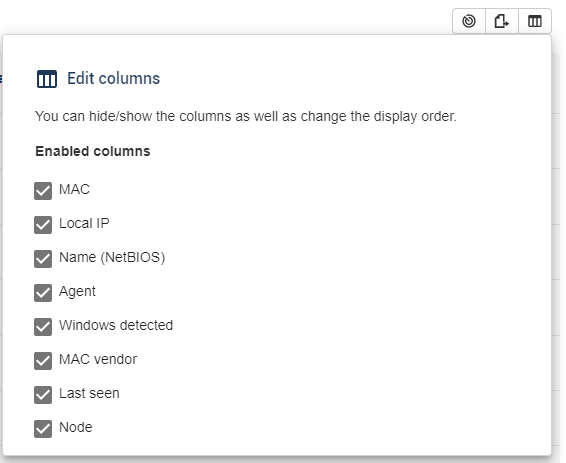
Columns edition
Pagination
Possibility to display up to 200 agents per page
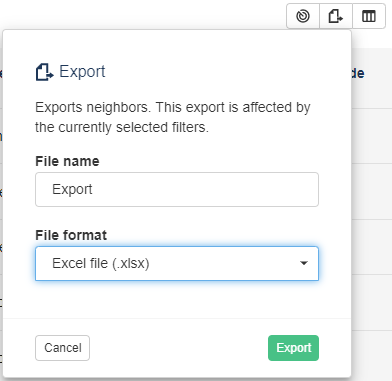
Export
Alerting
You can configure a new alert on the detection of a new neighbor. A New neighbor detected alert is available in the Heartbeat section of the Configuration / Alert page on an agent. You can associate it with the definition of an advanced expression in order to precisely filter the characteristics of the neighbor that will trigger the alert. The list of available filterable elements is like the columns on the Network neighborhood page. This data is accessible from the "event" object.
It is:
ip, mac, netbios, updatedAt, createdAt, macVendor, detectedOs, hasCorrespondingAgent
Example: I only want to be alerted for HP vendor neighbors with Windows as detected OS:
event.macVendor == 'HP and event.detectedOs ==' windows'
Wake-on-LAN
It is possible to power on a local network neighbor by sending it a Wake-on-LAN magic packet. For this, you can click on the Wake-on-LAN button of a neighbor, or select several neighbors and click on the Wake-on-LAN button on top of the page.

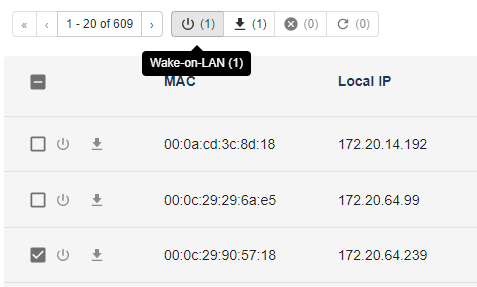
Beware, for that waking up to work, targeted neighbors have to be configured to accept Wake-on-LAN packets. The server agent have also to be turned on.
Agent deployment
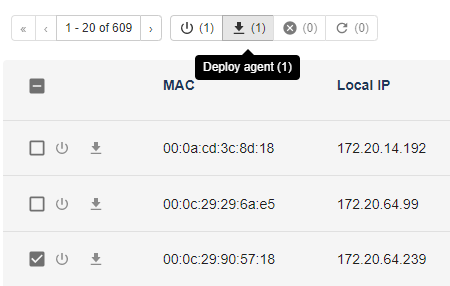
You can remotely deploy RG agents on Windows neighbor from the server agent. For this, you can click on the Deploy agent button of a neighbor, or select several neighbors and click on the Deploy agent button on top of the page.
You'll be invited to specify a Windows administrator credential for the targeted machines. If you target several neighbors, they have to share the same credentials. You can also specify in which node those agents will be deployed.
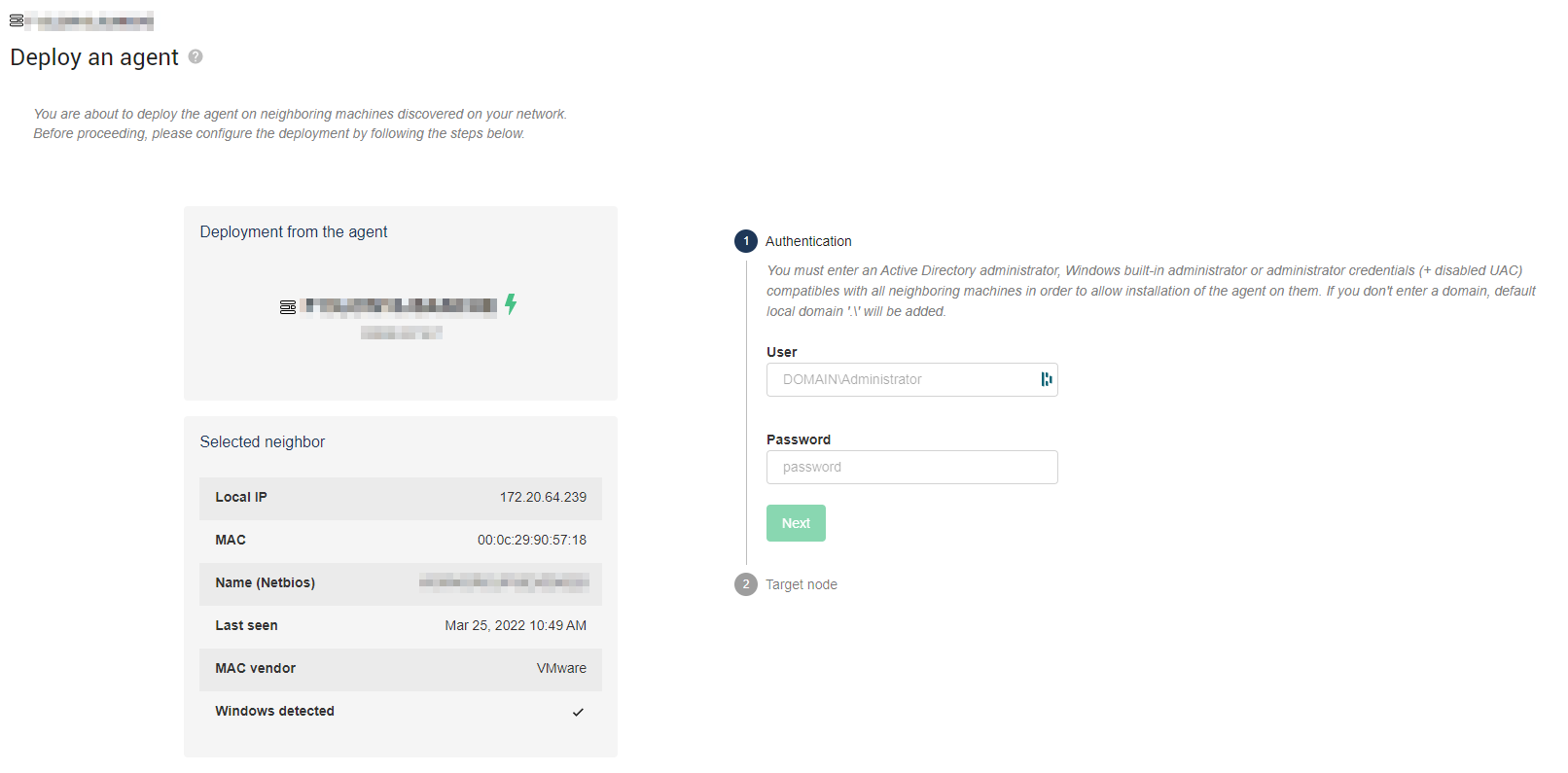
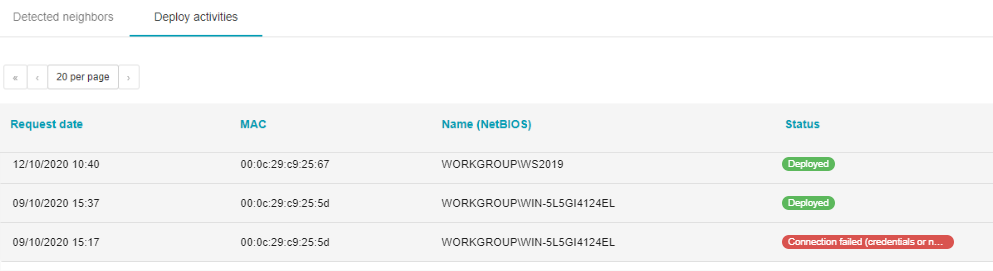
Once validated, an order is sent to the server agent, and those deployment will be done in succession. You can follow their roll-out in the Deploy activities tab.
A Windows RG agent will then be downloaded form RG cloud, and installed remotely by WMI. RG agent weight stay stable in time, with a size near 15 MiB.
Prerequisites :
- Targeted machines need to be at least on Windows 7 / Windows Server 2008 R2 (PowerShell 2.0 compatibility)
- Windows need to be installed on the C: disk of targeted machines
- WMI Remote service needs to be enabled on targeted machines (Windows Management Instrumentation service)
- Firewall need to accept WMI and DCOM connections
- On inquirer agent :
- Windows Management Instrumentation (WMI-Out)
- Windows Management Instrumentation (DCOM-Out)
- Sur les machines cibles :
- Windows Management Instrumentation (WMI-In)
- Windows Management Instrumentation (DCOM-In)
- On inquirer agent :
In order to deploy the RG agent, an Active Directory domain controller must be present in the network of the target machine. If this is not the case, a local account can be used with the following conditions:
- Either UAC is disabled on the target machines and local administrator credentials are used
- Either UAC is enabled and the default Windows Administrator account is used
To go further on the necessary WMI configurations, you can refer to this tutorial: https://docs.microsoft.com/en-us/windows/win32/wmisdk/connecting-to-wmi-remotely-starting-with-vista
Active Scan
Network neighborhood detection is done by a passive scan of the server agent's ARP table. This detection has the advantages of not impacting the network traffic, be light on resources, while being always active and real-time. You might however wish to do a more active detection of your local network, notably if this one doesn't have a central server (Active Directory server for example).
Active Scan will try a ping to every possible IPv4 addresses of the local network, thus forcing online machines to communicate with your server. Those communications are then caught by the ARP table passive scan system.
Beware, this scan can be long depending on the local network type (A, B or C), ensure the server will stay online during the entire scan duration. This feature is available since 2.3.5002 version.
Beware, in order for this detection to work, ICMPv4 traffic needs to be authorized by the Firewall:
- On inquirer agent : File and Printer Sharing (Echo Request - ICMPv4-In)
- On neighbors to detect : File and Printer Sharing (Echo Request - ICMPv4-Out)
FAQ
No neighbor appear on the page
The network neighborhood feature is available on Server agents since 2.3.4928 version. Ensure your agent is up to date and online.
Some machines of the local network don't appear
Only machines having communicated with your server are detectable by the RG agent. The best candidate to have a complete visibility is therefore the Active Directory domain controller, which communicate constantly with the local domain machines.
You can also force an active scan from your server.
Windows detected field is empty
This information is detected every 24h, if the target machine is offline another try will be done 24h later. Ensure also the firewall of server agent and neighboring machines are correctly configured.
Agent field displays an agent whereas the machine doesn't have one
This detection is based on MAC address uniqueness, it may be that this address modification, notably in the case of virtual machines. In those particular cases, it may happen that one or several agents are erroneously detected as being this neighbor. To ensure your parc safety, remote deployment is disabled on those neighbors, and you'll have to deploy RG agent manually.
Agent field displays several agents
This MAC address is used by several agents. Beyond above case, please check those agents aren't leftovers from reinstallation of which the previous agent hasn't been disabled.
Wake-on-LAN doesn't work
Ensure that your server is online, and that the target machine is configured to wake up on the reception of a Wake-on-LAN packet by its network interface.
Deployment error: RPC server is unavailable (Connection failed (credentials or network))
The deploying agent failed to contact the remote machine. Causes of this error can be:
-
The neighbor no longer exists or is not present in the network
-
The neighboring machine is switched off
-
A network problem prevents those machines to communicate
-
The neighboring machine doesn't check previously cited prerequisites
- One of the machines is not configured correctly (firewall blocking WMI/DCOM traffic, WMI service stopped)
-
A firewall blocks this traffic
To test the correct communication between your machines, you can launch this command from the deploying agent machine:
wmic /NODE:<IP> /USER:"<DOMAIN>\<USERNAME>" /PASSWORD:"<PASSWORD>" PATH Win32_OperatingSystem GET /value
While replacing <IP>, <DOMAIN>, <USERNAME> and <PASSWORD> fields by the remote machine parameters.
Deployment error: Access denied (Connection failed (credentials or network))
The deploying agent failed to authenticate on the remote machine. Causes of this error can be:
- Provided credentials are incorrect
- Provided credentials don't have required Administrator rights
- Provided credentials aren't those of the Active Directory Administrator and UAC isn't disabled
To test this, you can use the same command than above.
Deployment error: Already installed
The RG Supervision service already exists on the target machine. To ensure your parc safety, remote deployment is disabled on those neighbors. If you want to overwrite an agent to reinstall it, please do this operation manually.
Deployment error: Download and extract failed
The targeted machine couldn't download and extract the RG installer. Please try the operation manually on this machine to resolve this issue.
- Check that the directory C:\Windows\Temp exists
- Check in C:\Windows\Temp that the file rgsupv-win.zip exists. Else, the download failed. Confirm by trying to download from a web browser on the remote machine: https://dashboard.rg-supervision.com/download/rgsupv-win.zip (different URL on dedicated infrastructures)
- Check in C:\Windows\Temp that RG-Setup.exe, Tools and rgsupv_XXXXXX.txt exists. Else, try this extraction manually to see what can prevent it.
Deployment error: Register failed
Registration with our servers did not work, please try to run a network test via the RG agent interface from the remote machine: C:\Windows\Temp\RG-Setup.exe
If the deployment is done on an on-premise infrastructure, please check that the deploying agent has in its registry the key "expected-host-name" in HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\RG Systemes\RG Supervision\network configured with the correct value. If not, please fill it in and restart the deployment.
Beware, remote deployment won't work if your agent is configured to use a proxy.
Active scan don't display every local network machines
Ensure the inquirer server stay online during the entire scan. Neighboring machine also have to be turned on when they are interrogated. Finally ensure ICMPv4 traffic is allowed on the network and the different machines.